Avec Orange c’est l’enfer, impossible de monter une architecture stable … toujours des problèmes.
Normalement j’ai un NAT vers une IP locale, et ce NAT fait que j’utilise le certificat mis sur l’IP locale.
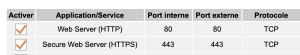 Quand je fais sur l’IP publique :
Quand je fais sur l’IP publique :
openssl s_client -showcerts -connect 80.15.48.50:443 CONNECTED(00000003) Can't use SSL_get_servername depth=1 C = FR, O = Orange, CN = Orange Devices Generic27 CA verify error:num=20:unable to get local issuer certificate verify return:1 depth=0 C = FR, O = Orange, CN = CCD42E-Livebox Fibre-JA20086CN001383 verify return:1 --- Certificate chain 0 s:C = FR, O = Orange, CN = CCD42E-Livebox Fibre-JA20086CN001383 i:C = FR, O = Orange, CN = Orange Devices Generic27 CA
Au vue du nmap c’est la gateway qui a une mauvaise information :
nmap -p 443 --script ssl-cert my.cyber-neurones.org Starting Nmap 7.60 ( https://nmap.org ) at 2020-11-10 10:33 CET Nmap scan report for my.cyber-neurones.org (80.15.48.50) Host is up (0.0013s latency). rDNS record for 80.15.48.50: laubervilliers-658-1-140-50.w80-15.abo.wanadoo.fr PORT STATE SERVICE 443/tcp open https | ssl-cert: Subject: commonName=CCD42E-Livebox Fibre-JA20086CN001383/organizationName=Orange/countryName=FR | Subject Alternative Name: IP Address:192.168.1.1, DNS:livebox | Issuer: commonName=Orange Devices Generic27 CA/organizationName=Orange/countryName=FR | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2020-02-24T10:42:58 | Not valid after: 2035-02-24T10:42:58 | MD5: d286 3014 37db 5f61 3200 bc17 1d06 f386 |_SHA-1: 8d58 ba94 db74 2d01 ca2c a1bd bcef b792 a558 bed1 Nmap done: 1 IP address (1 host up) scanned in 1.97 seconds
Par l’exterieur je n’ai pas de problème. C’est donc le DNS qui fait un mauvais routage :
# nmcli device show wlp64s0 | grep "IP4.DNS" IP4.DNS[1]: 80.10.246.2 IP4.DNS[2]: 80.10.246.129
Quand je fais sur le nom de domaine (en local):
openssl s_client -showcerts -connect sat.cyber-neurones.org:443 CONNECTED(00000003) depth=1 C = FR, O = Orange, CN = Orange Devices Generic27 CA verify error:num=20:unable to get local issuer certificate verify return:1 depth=0 C = FR, O = Orange, CN = CCD42E-Livebox Fibre-JA20086CN001383 verify return:1 --- Certificate chain 0 s:C = FR, O = Orange, CN = CCD42E-Livebox Fibre-JA20086CN001383 i:C = FR, O = Orange, CN = Orange Devices Generic27 CA -----BEGIN CERTIFICATE-----
Quand je fais sur l’IP locale j’ai le bon certificat (pareil si je passe par l’exterieur):
openssl s_client -showcerts -connect 192.168.1.42:443
CONNECTED(00000003)
Can't use SSL_get_servername
depth=2 O = Digital Signature Trust Co., CN = DST Root CA X3
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
verify return:1
depth=0 CN = sat.cyber-neurones.org
verify return:1
---
Certificate chain
0 s:CN = sat.cyber-neurones.org
i:C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
Voici l’erreur que j’ai :
$ curl https://sat.cyber-neurones.org:443 curl: (60) SSL certificate problem: unable to get local issuer certificate More details here: https://curl.haxx.se/docs/sslcerts.html curl failed to verify the legitimacy of the server and therefore could not establish a secure connection to it. To learn more about this situation and how to fix it, please visit the web page mentioned above.
Le probleme a commencé vers 02h du matin par surement un reboot de la livebox :
Nov 10 02:22:18 cyber-neurones kernel: [228577.565640] r8169 0000:01:00.0 enp1s0: Link is Down Nov 10 02:22:22 cyber-neurones kernel: [228582.503827] Generic PHY r8169-100:00: attached PHY driver [Generic PHY] (mii_bus:phy_addr=r8169-100:00, irq=IGNORE) Nov 10 02:22:23 cyber-neurones kernel: [228582.603989] IPv6: ADDRCONF(NETDEV_UP): enp1s0: link is not ready Nov 10 02:22:23 cyber-neurones kernel: [228582.810672] Generic PHY r8169-100:00: attached PHY driver [Generic PHY] (mii_bus:phy_addr=r8169-100:00, irq=IGNORE) Nov 10 02:22:23 cyber-neurones kernel: [228582.911994] IPv6: ADDRCONF(NETDEV_UP): enp1s0: link is not ready Nov 10 02:22:26 cyber-neurones kernel: [228586.152621] r8169 0000:01:00.0 enp1s0: Link is Up - 1Gbps/Full - flow control rx/tx Nov 10 02:22:26 cyber-neurones kernel: [228586.152649] IPv6: ADDRCONF(NETDEV_CHANGE): enp1s0: link becomes ready Nov 10 02:22:29 cyber-neurones kernel: [228588.543092] Generic PHY r8169-100:00: attached PHY driver [Generic PHY] (mii_bus:phy_addr=r8169-100:00, irq=IGNORE) Nov 10 02:22:29 cyber-neurones kernel: [228588.644106] r8169 0000:01:00.0 enp1s0: Link is Down Nov 10 02:22:29 cyber-neurones kernel: [228588.801614] Generic PHY r8169-100:00: attached PHY driver [Generic PHY] (mii_bus:phy_addr=r8169-100:00, irq=IGNORE) Nov 10 02:22:29 cyber-neurones kernel: [228588.903773] IPv6: ADDRCONF(NETDEV_UP): enp1s0: link is not ready Nov 10 02:22:32 cyber-neurones kernel: [228591.795592] r8169 0000:01:00.0 enp1s0: Link is Up - 1Gbps/Full - flow control rx/tx Nov 10 02:22:32 cyber-neurones kernel: [228591.795621] IPv6: ADDRCONF(NETDEV_CHANGE): enp1s0: link becomes ready Nov 10 02:23:26 cyber-neurones kernel: [228646.209283] r8169 0000:01:00.0 enp1s0: Link is Down Nov 10 02:23:29 cyber-neurones kernel: [228649.207082] r8169 0000:01:00.0 enp1s0: Link is Up - 1Gbps/Full - flow control rx/tx Nov 10 02:23:37 cyber-neurones kernel: [228656.568960] Generic PHY r8169-100:00: attached PHY driver [Generic PHY] (mii_bus:phy_addr=r8169-100:00, irq=IGNORE) Nov 10 02:23:40 cyber-neurones kernel: [228660.165981] r8169 0000:01:00.0 enp1s0: Link is Up - 1Gbps/Full - flow control rx/tx Nov 10 02:24:05 cyber-neurones kernel: [228684.699180] r8169 0000:01:00.0 enp1s0: Link is Down Nov 10 02:24:08 cyber-neurones kernel: [228687.606366] r8169 0000:01:00.0 enp1s0: Link is Up - 1Gbps/Full - flow control rx/tx
