Misère.


Misère.
UFC Que Choisir propose une page unique pour demander le retrait de ses données personnelles face aux démarcheurs et revendeurs de prospects :
https://www.respectemesdatas.fr/
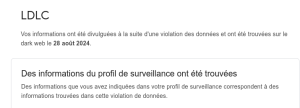
J’aime bien l’outil : https://haveibeenpwned.com/ , qui permet de voir si notre email est lié à une fuite.
J’ai fait le test sur mon email : 6 fois trouvés …
– Data Enrichment Exposure From PDL Customer: In October 2019, security researchers Vinny Troia and Bob Diachenko identified an unprotected Elasticsearch server holding 1.2 billion records of personal data. The exposed data included an index indicating it was sourced from data enrichment company People Data Labs (PDL) and contained 622 million unique email addresses. The server was not owned by PDL and it’s believed a customer failed to properly secure the database. Exposed information included email addresses, phone numbers, social media profiles and job history data.
Compromised data: Email addresses, Employers, Geographic locations, Job titles, Names, Phone numbers, Social media profiles
– Epik: In September 2021, the domain registrar and web host Epik suffered a significant data breach, allegedly in retaliation for hosting alt-right websites. The breach exposed a huge volume of data not just of Epik customers, but also scraped WHOIS records belonging to individuals and organisations who were not Epik customers. The data included over 15 million unique email addresses (including anonymised versions for domain privacy), names, phone numbers, physical addresses, purchases and passwords stored in various formats.
Compromised data: Email addresses, Names, Phone numbers, Physical addresses, Purchases
– LinkedIn: In May 2016, LinkedIn had 164 million email addresses and passwords exposed. Originally hacked in 2012, the data remained out of sight until being offered for sale on a dark market site 4 years later. The passwords in the breach were stored as SHA1 hashes without salt, the vast majority of which were quickly cracked in the days following the release of the data.
Compromised data: Email addresses, Passwords
– LinkedIn Scraped Data (2021): During the first half of 2021, LinkedIn was targeted by attackers who scraped data from hundreds of millions of public profiles and later sold them online. Whilst the scraping did not constitute a data breach nor did it access any personal data not intended to be publicly accessible, the data was still monetised and later broadly circulated in hacking circles. The scraped data contains approximately 400M records with 125M unique email addresses, as well as names, geographic locations, genders and job titles. LinkedIn specifically addresses the incident in their post on An update on report of scraped data.
Compromised data: Education levels, Email addresses, Genders, Geographic locations, Job titles, Names, Social media profiles
– Verifications.io: In February 2019, the email address validation service verifications.io suffered a data breach. Discovered by Bob Diachenko and Vinny Troia, the breach was due to the data being stored in a MongoDB instance left publicly facing without a password and resulted in 763 million unique email addresses being exposed. Many records within the data also included additional personal attributes such as names, phone numbers, IP addresses, dates of birth and genders. No passwords were included in the data. The Verifications.io website went offline during the disclosure process, although an archived copy remains viewable.
Compromised data: Dates of birth, Email addresses, Employers, Genders, Geographic locations, IP addresses, Job titles, Names, Phone numbers, Physical addresses
– You’ve Been Scraped: In October and November 2018, security researcher Bob Diachenko identified several unprotected MongoDB instances believed to be hosted by a data aggregator. Containing a total of over 66M records, the owner of the data couldn’t be identified but it is believed to have been scraped from LinkedIn hence the title « You’ve Been Scraped ». The exposed records included names, both work and personal email addresses, job titles and links to the individuals’ LinkedIn profiles.
Compromised data: Email addresses, Employers, Geographic locations, Job titles, Names, Social media profiles
Pour information la liste des Ranges Russes : https://lite.ip2location.com/russian-federation-ip-address-ranges
Autre information : https://www.numerama.com/cyberguerre/1269242-la-police-britannique-affiche-7-cybercriminels-russes-en-gelant-leurs-comptes-bancaires.html
Les anciens membres du groupe de cybercriminels Trickbot et Conti ont été identifiés par les forces de l’ordre britanniques. Ils sont à l’origine de l’un des malwares les plus dangereux de ces dernières années.
…
Tous ressortissants russes, ils ont participé à la préparation des attaques, au développement et à la gestion des logiciels malveillants, au vol d’infos ainsi qu’au blanchiment d’argent.